This is the second installment in a four-part series on cybersecurity and journalism. See part one, part three and part four.
Whether you’re a journalist, activist, or entrepreneur, there’s a good chance you’ll face a hacker or cyberattack at least once in your career. Unless you’re already a geek, you may find yourself at a loss for words when people start throwing around terms like DNS Amplification or lethality formula.
Not to fear: the following vocabulary terms can help you understand how cyberattacks work, and what you can do to help prevent them.
Bot-net: A network of computers that have been infected with viruses (also known as “trojans” or “malware”) that allow hackers to take over the computer’s functions. The hackers (sometimes known as “bot-herders”) then use the computers in this network to commit crimes anonymously.
C2, also C&C, or C2: Command and Control. How the bot-herders control a DDoS attack. If it’s via compromised computers and viruses, this is usually via a hacked server. Newer attacks performed by activists are organized via social media, forums, or chat programs. Typically, the activists identify a target, put out messages to recruit followers, and then use their social media accounts to tell everyone when to start or stop the attack.
CDN (Content Delivery Network): A service that handles the high bandwidth requirements of delivering content to a web site’s audience, especially important for sites that offer video or audio. CDNs are made up of many servers that are widely dispersed, which helps improve download speeds and makes CDNs more resistant to DDoS attacks.
DNS (Domain Name Server): When you type in a web address – such as http://sembramedia.org - into a web browser, you’re not actually entering the real address for the site. Computers cannot read human language; they deal in numbers. Thus, the SembraMedia.org site’s actual address, like any other site, is a really string of numbers separated by dots. A DNS associates those numbers with the human words or letters that we assign to it through the international agency known as ICANN (https://www.icann.org/).
DNS Amplification: A type of attack that uses internet protocols to boost the amount of traffic being sent at the targeted servers. An attacker sending out a packet of 60 bytes can use DNS amplification to bounce 4000 bytes back at the victim – basically about a 70:1 amplification that allows a small bot-net to strike like a much larger one.
IOT (Internet Of Things): A term that refers to the growing practice of building internet connections into “smart” devices, such as refrigerators, thermostats, security cameras, etc., that allow them to be controlled remotely. Unfortunately, many of these new devices have weak security, making it relatively easy for them to be hacked and used as part of a bot-net. Many of the largest and most recent DDoS attacks leveraged IOT devices.
Layers: This is a highly technical term that refers to how the hackers are attacking a site. In the generally accepted model, there are seven layers to the internet that range from the actual physical wiring that carries the signals (Layer 1) to the browser that runs on your device (Layer 7). Most serious DDoS attacks take place on Layer 3 or 4, which are the ones associated with how servers talk to each other. For more, visit http://www.webopedia.com/quick_ref/OSI_Layers.asp.
Lethality: Experts calculate how bad a DDoS attack is via this formula – No x Bw x La x Co = Le, where:
- No = the number of Nodes attacking (i.e. number of hacked computers)
- Bw = average Bandwidth of the nodes
- La = the layer in the OSI “technology stack” where the attack is being staged
- Co = the Coordination of the attack by the hackers (i.e., are all the infected computers attacking at the same time, and do they keep attacking)
- Le = Lethality of the attack.
So, an attack by 4,000 hacked computers, each with high-bandwidth internet connections of 10Mb/second, on Layer 3 (scored as a 1.0), where 75 percent of the computers are acting in perfect unison, would look like this:
4000 x 10,000,000 x 1 x .75 = a 30Gb/sec attack.
Some of the different DDoS attacks you may face include ping-of-death (POD) attacks, Slowloris attacks, RUDY attacks and smurf attacks. It's important to know the difference.
Load-Balancing: A mitigating response to a DDoS attack that uses networks of “Good Guy” servers to try to help each other out when one of them comes under attack. System administrators use load balancing to route traffic from overloaded servers to ones that have spare capacity. For example, Amazon’s “Elastic Beanstalk” uses load balancing to keep a website online when traffic spikes thanks to a piece of content going viral. The problem: on premium services, websites get charged for bandwidth, and the more you use, the more you pay. Warning: bills can quickly hit US$10,000+ per MINUTE if a site is under a large attack.)
LOIC (Low Orbit Ion Cannon): Named after a deadly weapon in a popular videogame, the LOIC is an attack script that can be run by one person, or a small group of people on their own computers. The program causes the hacker’s computer to open as many as 256 connections at the same time to the targeted site and then start flooding it with nonsense traffic. On its own, this can be no big deal, but activist groups like Anonymous, which has thousands of members, have used this technique to take down very large targets such as Visa, PayPal, and Sony.
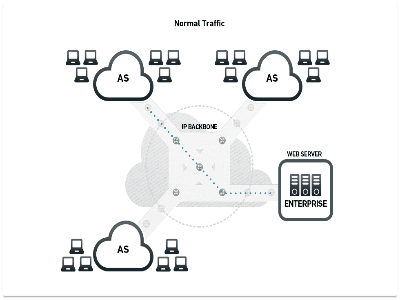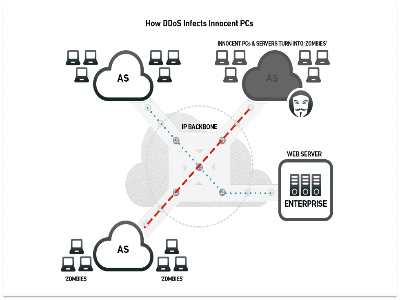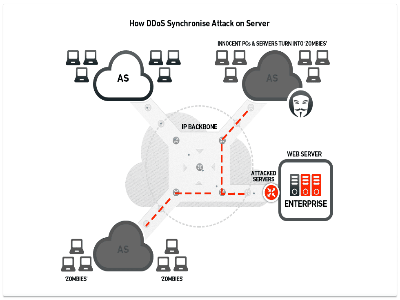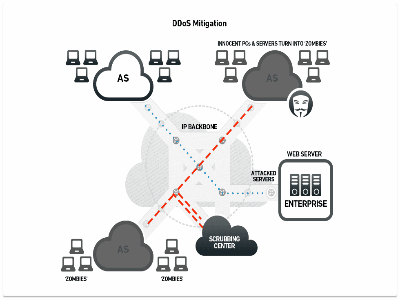 Origin Server: The primary server in a chain of servers that host a site. For example, an online newspaper may have one primary origin server that contains all the stories, photos, videos, etc. that it wants to publish. That origin server then distributes that content to a network of other servers, configured so that if a lot of traffic gets directed at one, the others can step in and start to take up the load. Sophisticated DDoS attacks target the origin server to take down otherwise large and resilient sites.
Origin Server: The primary server in a chain of servers that host a site. For example, an online newspaper may have one primary origin server that contains all the stories, photos, videos, etc. that it wants to publish. That origin server then distributes that content to a network of other servers, configured so that if a lot of traffic gets directed at one, the others can step in and start to take up the load. Sophisticated DDoS attacks target the origin server to take down otherwise large and resilient sites.
Packet: A tiny data file. Most information sent across the internet is chopped up into these tiny pieces, or packet files, rather than being sent as one big file.
Ping: Named and modeled after a procedure used in submarines, in which sonar operators send out a high-pitched sound and listen to hear the echo. Pings are not malicious in and of themselves; they are actually a common feature of internet communications wherein one computer sends a short burst of data (a packet) at an IP address to see if there is actually a computer there to receive it. The computer at that address responds with a short burst of data to say, “Yes, I am here.”
POD (Ping of Death): Computers talk to each other using information in packets of 56 or 84 bytes at a time. During a POD attack, hackers send packets of up to 65,535 bytes, causing the computer or server receiving this packet to have the electronic equivalent of a nervous breakdown.
Recruitment: How many and how quickly the hackers can add nodes (i.e., hacked computers) to a DDoS attack. Depending on how good the hackers’ C2 is, they can issue orders to thousands of hacked computers all at the same time – or it can take hours for all the nodes to come online for peak traffic. Slow and spotty recruitment is often an indicator that a DDoS attack is being organized via social media, with activists telling their followers, “Hey, flood this site with traffic and take it down.”
RUDY (R-U-Dead-Yet): A DDoS attack variant where the hackers find a contact form on your site and then use their compromised computers to fill it out very slowly. Your server will think that the attackers are legitimate users and maintain a data connection to them so they can fill out the form. When there are too many persistent data connections filling out forms on your server, it becomes overloaded and crashes.
Slowloris: Unlike some other DDoS attacks, this one can be performed by a single computer running a script. Like a RUDY attack, the Slowloris overwhelms servers by opening up connections, and then doing just enough to make sure the targeted server doesn’t disconnect.
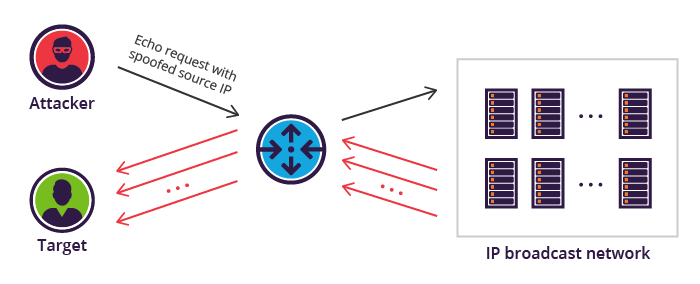
Smurf Attack: An ingenious variation of the common DDoS attack, where the attackers spoof the IP address of your site, and then send out ping traffic to thousands of computers (see above image). The other computers respond to this ping by sending an acknowledgment back to the IP address – your computer. The smurf attack makes it look like your computer is the bad guy, hitting thousands of other computers with junk traffic.
Spoofing: Faking the origin of an attack, so that it looks like the source of the traffic hitting your server is coming from all over the world, when it is actually only coming from a group of computers (often in a school or business) where the hacker has compromised the machines.
UDP Flood (User Datagram Protocol): Also known as “alphabet soup” attacks, these use a type of web connection usually reserved for chat apps or VOIP phone calls, in order to trick servers into opening up a connection. The attacker then uses that connection to flood the server with junk packets. When the server tries to make sense of the packet, it becomes overloaded.
Whitelisting: Another tactic used to manage DDoS attacks. Instead of “blacklisting” or banning IP addresses as they prove to be malicious, “whitelisting” helps your server to identify traffic from trusted IP addresses. This is kind of like the now-common practice of whitelisting emails that come from a person or company that you like, so they don’t wind up in your spam folder.
Main image and secondary images CC-licensed by Wikimedia, via Singtel, Arielinson, and Imperva Incapsula.

