Now more than ever, when malicious software programs are highly effective at cracking our social media, email and other accounts, journalists must be vigilant about protecting their passwords.
Effective password protection means taking steps to safely guard access to information about your contacts, confidential sources and research documents.
Journalists must take time to think about their passwords, measure their strength, change them regularly, keep them organized and make them available in a secure file.
This need is even greater in high-risk contexts, such as reporting on corrupt officials or businesses, or when investigating the activities of a criminal organization. In such cases, neglecting the security of passwords can endanger the physical safety of our sources and colleagues.
Elements of a secure password
A strong password should have 15 characters, including lowercase letters, uppercase letters, numbers and symbols such as punctuation marks. Strong passwords do not use personal information, words that appear in the dictionary in any language, common names or your login name. Strong passwords are not the same as or even similar to your previous passwords, and they never include keyboard patterns such as “QWERTY,” “asdfghkl” or “1234567.”
Avoid brute force attacks
Complicated passwords help you protect your devices and information from malicious programs that try to crack your password. These are known in digital security parlance as brute force attacks.
Our main goal in strengthening our passwords is to avoid becoming easy targets for brute programs, which frequently crack passwords by replacing the letters and numbers that people commonly use to strengthen their passwords. For example, many people replace the number zero (0) with the letter “O”, the letter “I” with the number “1,” or the letter “S” with the dollar sign symbol “$.”
Beware of online tricks
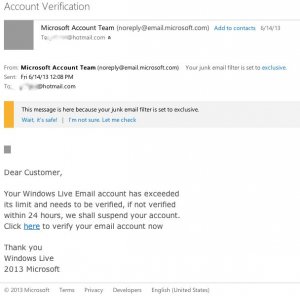
A second step is to protect our passwords from attempts at "social engineering" that arrive in our email inboxes. The image below is an example of a social engineering operation to "crack" our hotmail account. If we click the active link that comes in a message like this, we will likely lose control of the account.
Crafting a strong password
One way to build a strong password is to start with a phrase from a poem or song. For example, I could build a strong password using the third sentence of the song "Three Words" by Luis Miguel, a famous Mexican singer: “Con tres palabras te diré todas mis cosas.”
Here’s how to do it:
-Step 1: Write out the whole phrase in lowercase with no spaces: contrespalabrastediretodasmiscosas
-Step 2: Change some of the letters from lowercase to uppercase at random: coNtrespalabrAsTedirEtodAsMiscosaS
-Step 3: Add a few numbers: coN3trespalabrAs2TedirE5todAsMis7cosaS
-Step 4: Add a few random symbols: CoN3tres #palabrAs@2Te%dirE5todAsMis^7cosas
This is a password that would be hard for anyone to guess or to crack.
Generating random passwords
One way to ensure your passwords don’t contain personal information is to randomly create them. The site Strong Password Generator allows us to quickly create a random and strong password. Here is how:
Step 1: Go to the site Strong Password Generator. Step 2: Choose a password length of 15 or more characters. Step 3: Choose a password format that contains punctuation. Step 4: Click, "Generate the password": The program gives you a password like this: )'M<:! Qi4ZdO"'H Step 5: The program also gives you a mnemonic device for remembering the password. In this case, it is: ) "MIKE <:! ZULU delta QUEBEC OSCAR india 4 "'HOTEL" Save this version, then you can shorten it when you need to enter it later.
Save your passwords safely
By now you must be wondering, "Just how do I remember all of these complicated passwords I'm supposed to create?" Many of us have between 10 and 50 passwords or even more, depending on how many accounts and devices we use in our daily lives and in our work. It’s tempting to simplify your passwords or to not replace them regularly once you finally have them all memorized. Don't give into that temptation.
Fortunately, there are some programs that can help. Check out KeePass, a site which lets you stash your passwords in a secure folder online instead of writing them on paper or in unencrypted files on your computer.
To get you started, here's a tutorial on how to install KeePass.
MacBook computers have a built-in system called "Keychain Access," in which you can manage and store passwords in encrypted form.
Of course, you will have to create and memorize one strong password to open the password management programs.
An additional advantage of using these systems is that you copy and paste your passwords instead of typing them. This lets you reduce the risk that your password gets hacked by a malicious program that records what you type on your computer keyboard.
Use two-step authentication
Some platforms, including Gmail, Twitter and Facebook, allow you to install an application to create a dual system of authentication. With these systems, in addition to your password, you enter a secret code that is sent to your mobile phone. Gmail allows you to link your account with an authenticator application. Instead of sending you a text message, the application generates a numeric password and you enter that.
Additional tips to keep in mind
- Never use your passwords to open your accounts over an open wifi network.
- Use an antivirus program to detect malicious programs that record what you type on your keyboard.
- Beware of video cameras that might be recording what you type on the keyboard.
- Be careful of people who might be looking over your shoulder when you type in a password at cafes, libraries or airports.
- Choose a different password for each of your accounts.
- Measure the strength of your password at PasswordMeter.
- Change your passwords frequently.
- Do not recycle your passwords.
- If you find any sign that your account has been cracked, change your password immediately.
- On social networks such as Facebook and Twitter, choose the option that requires you to enter a personal identification number (PIN) whenever you attempt to open records from a new IP (Internet Protocol) address.
If you use these tips, please let us know in the comments.
Jorge Luis Sierra is a Knight International Journalism Fellow developing digital tools for citizens and journalists to map crime and corruption. He focuses on digital and mobile security.
This post was translated from Spanish into English and edited by Jennifer Dorroh.
Image CC-licensed on Flickr via binaryCoco.

